Google has multiple different official blogs (for example blog.google, firebase.googleblog.com, or cloud.google.com/blog).
Blogs on *.googleblog.com are hosted on blogspot.com and uploaded images are hosted on Blogspot’s CDN. However, The Keyword (blog.google) and Google Cloud blog use a custom platform for their blogs.
Images on these blogs are stored in Google Cloud Storage buckets:
https://storage.googleapis.com/gweb-uniblog-publish-prod/and
https://storage.googleapis.com/gweb-cloudblog-publish/respectively.
Google Cloud Storage is an IaaS file storage service on the Google Cloud Platform and can allow us to access the resources via an URL on the web.
Accessing the buckets
We can access the bucket in the browser using one of these URLs:
https://storage.googleapis.com/<bucket name>/https://<bucket name>.storage.googleapis.com/https://storage.cloud.google.com/<bucket name>/https://sandbox.google.com/storage/<bucket name>/
and adding the filename at the end of the URL.
The Keyword Blog
However, if we try to access the first Cloud Bucket in the browser, it shows that we don’t have permission to list the uploaded items.
<?xml version="1.0" encoding="UTF-8"?>
<Error>
<Code>AccessDenied</Code>
<Message>Access denied.</Message>
<Details>Anonymous caller does not have storage.objects.list access to the Google Cloud Storage bucket.</Details>
</Error>That’s because public listing of uploaded items is disabled by default.
Google Cloud Blog
But if we try to access the second bucket, it returns the list of all uploaded items in the bucket.
<?xml version="1.0" encoding="UTF-8"?>
<ListBucketResult xmlns="http://doc.s3.amazonaws.com/2006-03-01">
<Name>gweb-cloudblog-publish</Name>
<Prefix />
<Marker />
<NextMarker>images/100-announcements-12_T3T5Cv5.max-300x300.png</NextMarker>
<IsTruncated>true</IsTruncated>
<Contents>
<Key>images/-02-MAIN-Dublin.2e16d0ba.fill-1000x347.jpg</Key>
<Generation>1529607698661849</Generation>
<MetaGeneration>1</MetaGeneration>
<LastModified>2018-06-21T19:01:38.661Z</LastModified>
<ETag>"fbce0d28ed561e2248946ca8763de8ad"</ETag>
<Size>156772</Size>
</Contents>
<Contents>
<Key>images/-02-MAIN-Dublin.2e16d0ba.fill-1000x563.jpg</Key>
<Generation>1529607698725002</Generation>
<MetaGeneration>1</MetaGeneration>
<LastModified>2018-06-21T19:01:38.724Z</LastModified>
<ETag>"a22b9d844cb2ade708ce4166f7d4797e"</ETag>
<Size>259746</Size>
</Contents>
<Contents>
<Key>images/-02-MAIN-Dublin.2e16d0ba.fill-100x100.jpg</Key>
<Generation>1529607698808132</Generation>
<MetaGeneration>1</MetaGeneration>
<LastModified>2018-06-21T19:01:38.807Z</LastModified>
<ETag>"ec3c2c4d8bff33d050e251a40a7ee52d"</ETag>
<Size>7264</Size>
</Contents>
…
</ListBucketResult>Why did this happen? This bucket had public view permissions added for everyone.
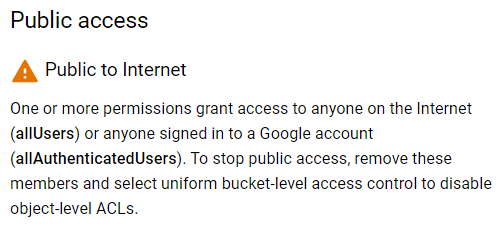
Since the Storage Object Viewer (roles/storage.objectViewer) permission (or roles/storage.legacyBucketReader) has been added for allUsers, it allowed anyone to view and list items stored in the bucket.
Storage Object Viewer
Grants access to view objects and their metadata, excluding ACLs.
Can also list the objects in a bucket.
Impact
The bucket was accessible to the public and included all uploaded images on the Google Cloud Blog, including images in draft blog posts.
Getting access to images that have not been published yet could have resulted in a leak of confidential information, for example, upcoming Google Cloud products or features.
| Timeline | |
|---|---|
| 2019-04-10 | Vulnerability reported |
| 2019-04-10 | Priority changed to P2 |
| 2019-04-10 | Looking into it |
| 2019-04-12 | Filed a bug |
| 2019-04-16 | Reward issued |
| 2019-04-24 | Marked as fixed |