Attacker can get access to the victim’s CodeJam account and read and edit their profile information (address, phone number, etc).
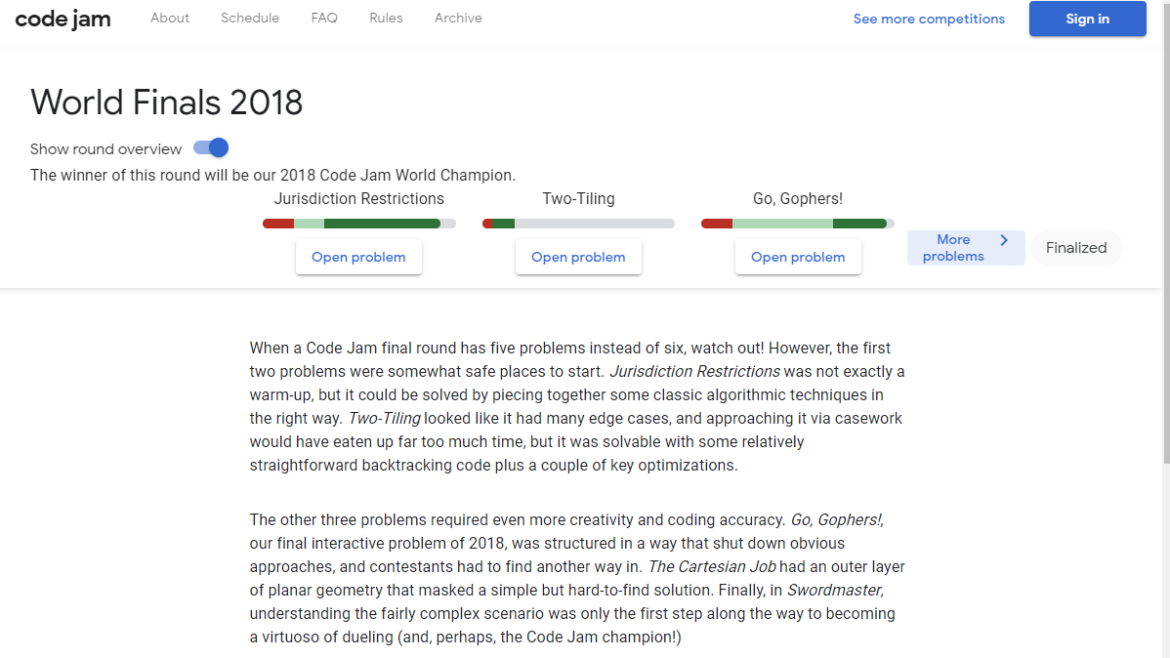
Thomas Orlita’s blog

Attacker can get access to the victim’s CodeJam account and read and edit their profile information (address, phone number, etc).
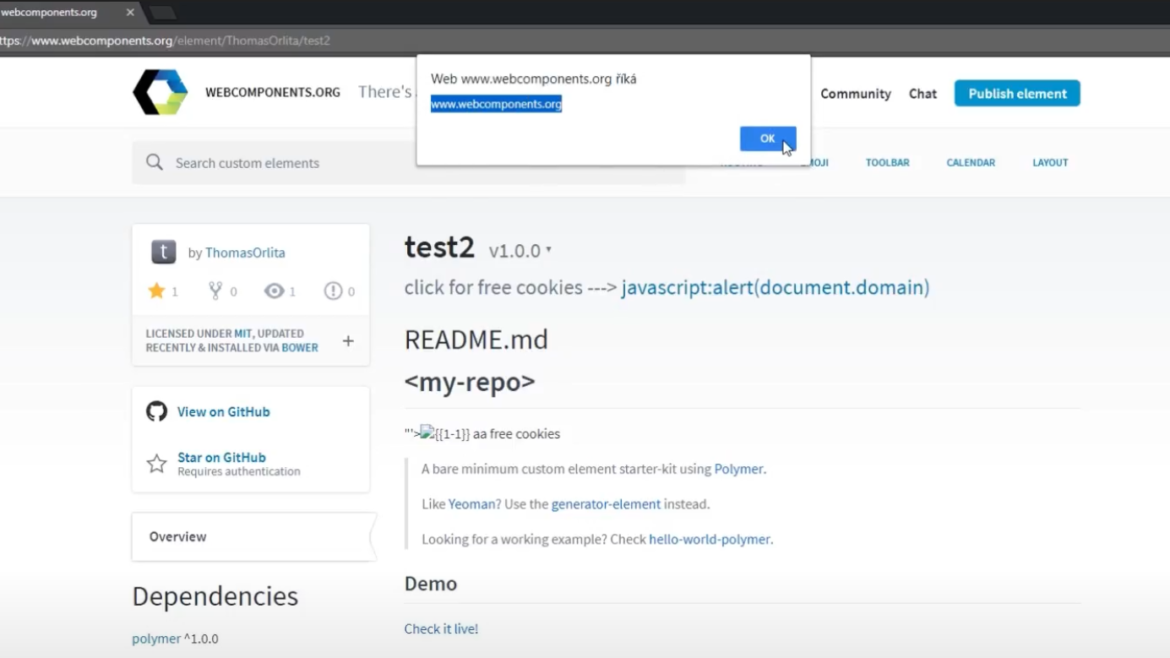
If the user has authenticated using Github on webcomponents.org before, it’s possible to get the Github auth code and use it to star any public Github repo behalf of the user.
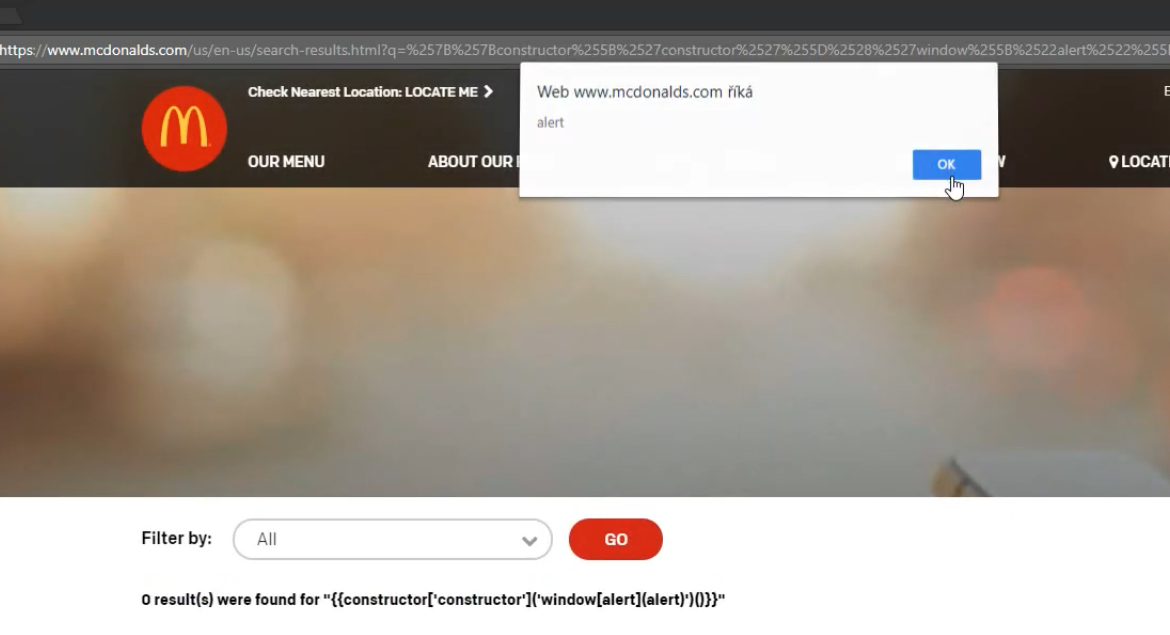
I reported this vulnerability on https://www.openbugbounty.org/reports/608322/ Previous fixed vulnerabilities on mcdonalds.com: https://www.openbugbounty.org/reports/481416/ < back to the list of web vulns